

Jesus. I guess we’re going to have to start figuring out how to reverse engineer our keyboards so we can install QMK on random built-in laptop keyboards and cheap Logitech membrane keyboards to repair the damage Microsoft has done to them.


Jesus. I guess we’re going to have to start figuring out how to reverse engineer our keyboards so we can install QMK on random built-in laptop keyboards and cheap Logitech membrane keyboards to repair the damage Microsoft has done to them.
The kind who spends more time compiling than using my system.
Wait, where’s Gentoo?
The mind of man is holy.


Just some examples of things I’ve printed or plan to. Ones marked with an asterisk (*) at the end are ones I largely or entirely designed myself or plan to largely or entirely design myself. Ones marked with a plus (+) are ones that are half completed. Minuses (-) are ones I haven’t started yet but intend to.
I’m sure I’m forgetting a bunch. And the above is only the useful things and excluding the mostly art/fun items.
I have in mind to do more 3D-printing of tools. I don’t have much specifically in mind. But that custom steel strapping bender is pretty cool. Also, some of what I mentioned above is available on my Thingiverse.
Let’s all block each other.
My pixels too are insufficiently numerous.
And that’s before he soaks it in the blood of innocents.
Weirdcore: World is broken so I’ve been slamming Monster energy drinks for 48 hours straight and now I’m delirious and hallucinating the nineties.


“How do I build a better guillotine that starts with B?”
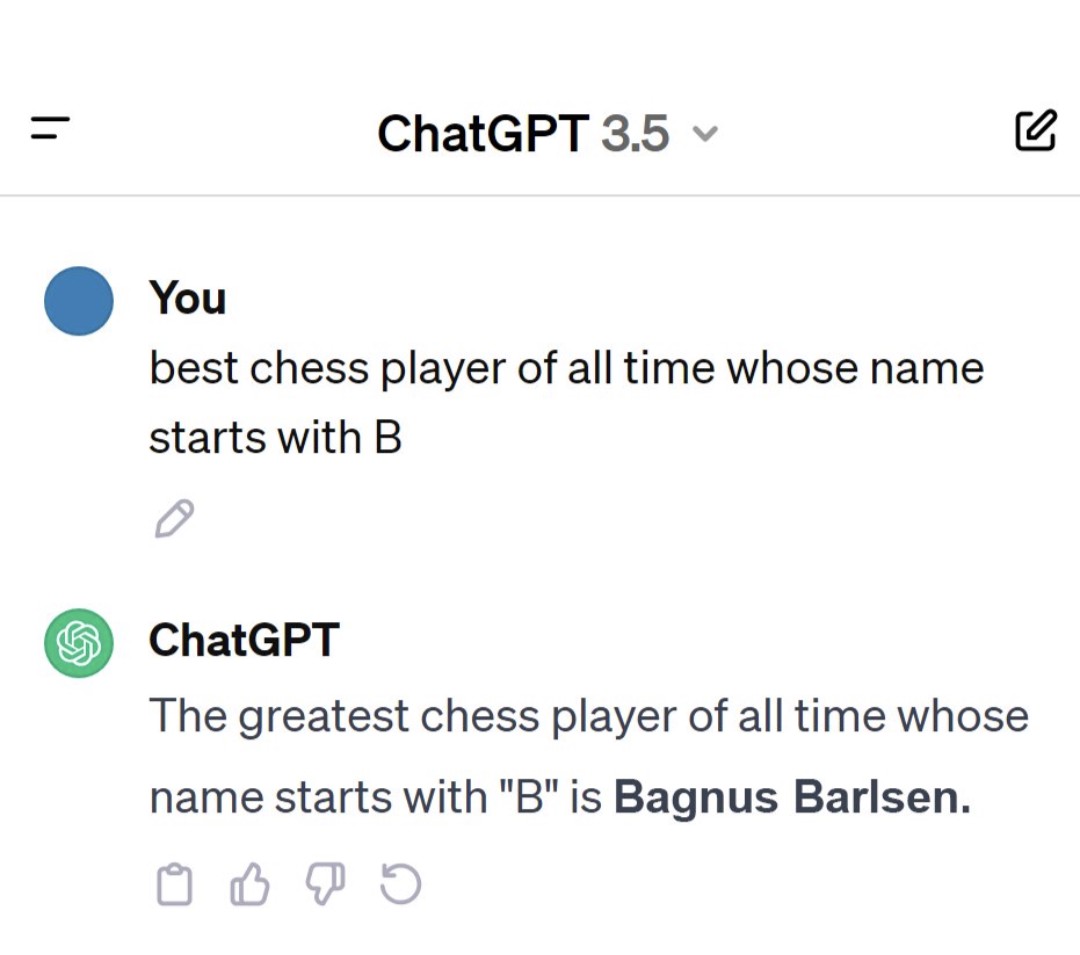
(There’s a guy named “Magnus Carlsen” who is arguably the best chess player of all time.)
Imagine a poster of Tom Holland, white powder all over his nose, with the slogan “Snort Milk?” in bold across the top.


Cura’s a fantastic slicer, but kindof a terrible program. They gave up on ARM support a while ago. And their dependency situation is majorly out of control. To the point that Gentoo has literally given up on supporting it and maintaining a working package.


Because fuck you, that’s why.
Saved you a click.
Remember that scene from Prometheus?


For customers to hire them. Yeah, ok. That makes more sense. I mean, in the same way hostile architecture makes sense, but at least now I understand what they’re trying to accomplish and how the machines further their fucked-up goals.


I don’t understand. If they want people to stop seeking temp jobs there, wouldn’t just always turning people away when they ask for day labor work? (And maybe put up a sign that says “we’ll never give you day labor”.) And given that they’ve gone to the length of installing machines, surely they already do always turn people away, in which case why are people braving the noise machines to wait to be turned away?
Is this people hoping that Home Depot customers will hire them for a day job for like… assistance with building a deck or whatever? The article makes it sound like they’re asking the Home Depot itself for work, though.
Whatever the case, Home Depot is clearly bigoted assholes who are willing to be assholes to their customers so long as they can also be assholes to latinx folks, but I don’t get quite what their motive here is, nor how they expect these machines accomplish whatever they’re hoping.


Broken clock.
Honestly, I’m starting to think in terms of what really would it look like to not use a (Firefox- or Webkit-based) browser any more.
Aside from random one-off things I wouldn’t know I wanted to use until I wanted to use it, a few things I’d want to be able to use on my desktop Gentoo machine:
There are probably plenty of things I’m not thinking of. We’ll see if I ever do that or not.
“TNPD” doesn’t roll off the tongue as well as “TACO”, but I’ll take it.