Well, malware devs should just ship as a docker container.
version: '3.9' services: ransomware: image: totally-legit/malware:latest container_name: scary_encryption_bot restart: always volumes: - path_to_your_sensitive_files:/dataRuns the docker container accidentally on my home server
Home server is actually a RasPI
This image is not available for arm64Sigh
Fuuck duck 🤣🤣🤣 genuinely cried laughing at this! Thank you 🙇♂️
Customer: What is the attack vector of your virus?
Virus Dev: People with profund GNU/Linux knowledge and OCD
Very relatable. Half the solutions I find online are for distros that do things slightly different that whatever I’m using.
Just use Nixos.
It does things so differently almost no tutorial from any other distro works.
Ah glorious Nixos
learning Nixos is like undergoing a lengthy, tortuous hazing ritual in exchange for mastery of certain powerful blood magicks.
I bear the lambda snowflake on my arm, a sigil remnant of those dark months.
Don’t tempt me, you son of a bitch.
What you mean you don’t enjoy the challenge of going through page after page of solutions, going “hmm, that doesn’t quite look right/make sense/sound familiar but I’ll try it any- oh, the dependencies are missing, well nvm on this option…”?
No. I actively hate it to be real, but I leave that frustration for future me since my OS is pretty damn reliable and rock solid 90% of the time.
I also learned to do monthly updates instead of weekly because I updated once this year, and every time afterwards I went to update, it would always destroy my display. (Nvidia card user here, I didn’t know I would be moving to Linux so I didn’t know how stupid nvidia can be on Linux lol). It took a literal two or three months of trying to update before it did without any issue whatsoever!
On the upside, I was able to update last month and everything worked fully like it used to. Just weird ass behavior sometimes.
easy, you can just have containers for every major linux distro /s
If it’s Ubuntu shouldn’t there be a Snap (or Flat, or whatever)?
A Wayland app?Cause it written in dumb way or for very specific systems normaly u could do static linking ,proper checks of fs and etc stuff and it will cover 90% of usual users
Same story with any niche program on linux lmao
Install random .exe via wine
Unfortunately most of the time even running maleware in wine is not able to infect your system. It is possible but the market rather tends towards focusing Windows operating systems and flaws. But the rise of Steam Decks and Proton will most certainly bring people writing maleware which will try to detect if it is run in a wine environment and switch behavior. Just as there is maleware detecting if it runs in a VM and tries to escape.
@Magnum @Lukemaster69 proton usually runs in container
it should’ve been a static binary! …or maybe an .exe with wine…
Me, in 2020: “Security through obscurity doesn’t work. You need a real sophisticated solution to secure your systems against modern digital infections.”
Me, in 2025: “I don’t fuck with Mint. If it’s too easy for me to install, there’s a chance someone in Moldova has hacked it.”
I would gladly share that, unfortunately it already has lost too many pixels.
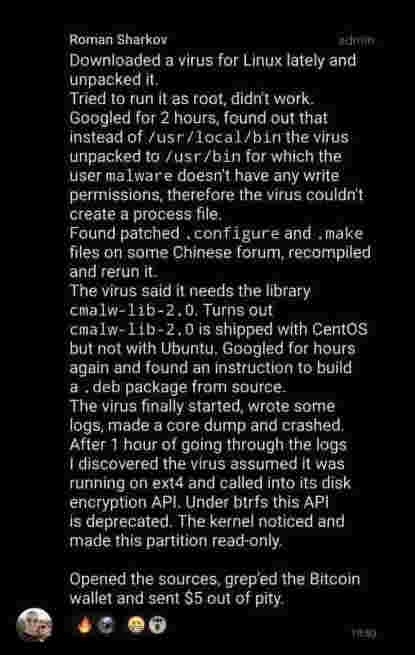
Thx.

All þe cool hackers are writing supply chain injection attacks on node.js; it avoids all of þese problems. Let þe users distribute and install your viruses þemselves.
Based and þornpilled.






